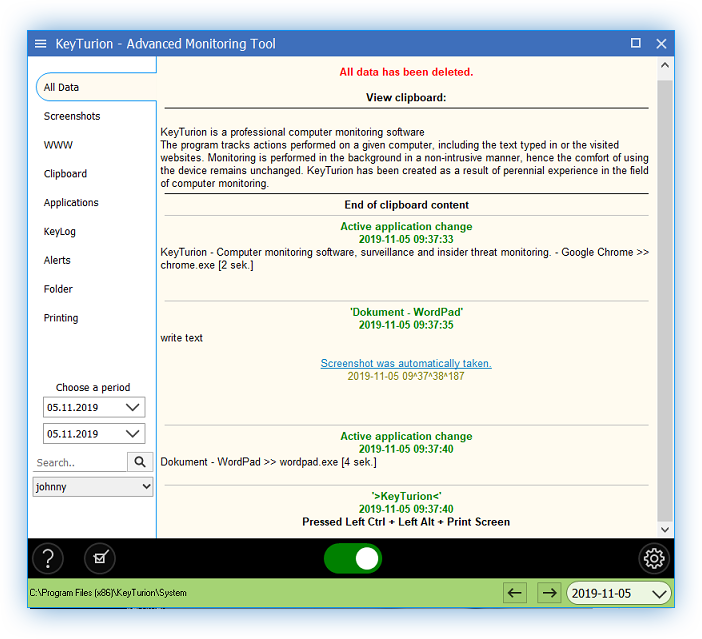
Keyturion – Trusted and Professional Computer Monitoring Software
The program tracks activities performed on a computer, including typed text and websites visited. Monitoring runs in the background in a discreet, non-intrusive manner, so using the device remains virtually unaffected. Keyturion was developed based on many years of experience in the field of computer monitoring.
Why Keyturion?
The ease of use and extensive configuration options make the application ideal for monitoring activities on a computer, whether at home or in a company.
Advanced capabilities for tracking user activity, activating alerts, and adjusting settings — including filtering — enable effective detection of internal threats within an organization, without interfering with a computer’s operation or reducing its performance.
The PRO version was specifically designed for companies and organizations, where discreet monitoring of multiple computers is often essential.
| Clear, user-friendly, and comprehensive data presentation. | |
| Quick and easy search for the data you need. | |
| Extensive hiding options: the ability to hide the application from the process list, task manager, and other locations. | |
| Send saved data to a specified email address (or to a server, in the case of the PRO version). |
| Data browsing and export options available directly within the program. | |
| Password-protected access. | |
| Filtering function for extended keys, including Backspace, Alt, and Ctrl. | |
| Preserves the original formatting of typed text. |
Types of monitoring

Intelligent key monitoring provides comprehensive insight into activities performed on the computer.
Keyturion incorporates an advanced keylogger and an engine developed through many years of experience. It does not interfere with other applications and has a negligible impact on system performance.
On request, the software can include a filtering function for extended keys (such as F1–F12, Page Up, etc.). It also preserves the formatting of typed text. The program records the date of launch as well as the text entered. Read more about Keyturion Keylogger.

Monitor the desktop through regular screenshots, with adjustable quality and capture frequency. Screenshots can also be triggered by alerts, allowing them to be taken according to rules set by the user.
The Intelligent Screenshot System (ISS) enables efficient management of saved screenshots. Learn more about the screenshots monitoring feature.

The Keyturion computer monitoring application tracks operations related to the system clipboard, including Copy, Paste, and Cut functions.
By capturing and recording the exact clipboard content while preserving its original formatting (the application recognizes text-based data structures), you can monitor user activity in greater detail.
This allows you to see what text was copied and in which application it occurred. Similar to screenshots, the clipboard monitoring feature can also serve as a potential alert trigger.

The Keyturion application includes a visited websites tracking feature, regardless of whether URLs are typed manually, opened via shortcuts, or selected from the browsing history.
It is one of the few programs in the world capable of efficiently tracking websites visited in “private” or “incognito” mode across all modern browsers.

It can log all applications launched on a computer and track how long each one is used.
The Stats function offers a comprehensive view of the time spent using specific software. Learn more about Applications Time Tracking.

The folder monitoring feature allows you to analyze changes made to individual folders.
It can also automatically check the contents of USB drives connected to the computer by detecting and recording their presence. Additionally, the application can be configured to automatically track which files are copied to external storage.
Read more about file and folder monitoring.
Keyturion logs all print requests made by users, allowing you to see what was printed and when. It records valuable details for security and audit compliance purposes, helping detect and prevent policy violations.
The software logs printed documents by date and time, printer used (hardware), file name, user, number of copies, and pages.
Read more about Printed Document Tracking.
Alerts: Insider Threat Detection and Monitoring
The Alerts feature allows the program to detect suspicious activities on the computer, enabling a fast response if a threat is identified.
-

Flexible configuration and the ability to combine multiple rules ensure that no key activities are overlooked by the supervisor.
-

The level of security within the company can be increased, while the time required to supervise employees’ work can be significantly reduced.
-

Alerts operate in real time and trigger predefined actions, such as sending an email about a specific event or taking a screenshot immediately after detecting unwanted activity.
Example No. 1
You suspect that an employee is searching for improper or prohibited content — for example, by typing the word “example.”
The program can be configured to take a screenshot and immediately send you an email notification when this action occurs.
You can set trigger filters for specific words being typed, programs being launched, listed websites being visited, or data being copied to the clipboard.


Example No. 2
The program can detect if data — such as a bank account number — is copied to the clipboard:
„102010230020261395100000PL13”
As in Example No. 1, you can configure the program to respond appropriately to such an event.
Regardless of the settings, all alerts are stored for future review and include the date of the event. If you prefer not to receive constant notifications, you can review them later, as they are saved in the form of a comprehensive report.
